How to protect your website from Hackers
What is Web Server and Hacking?
Websites are hosted on web servers. Web servers are themselves computers running an operating system; connected to the back-end database and running various applications. Any vulnerability in the applications, Database, Operating system or in the network can lead to an attack on the web server. A web server is widely considered to be a hardware computer but in addition to the hardware, software computer application installed on the hardware computer is also the web server. The primary function of a web server is to deliver web pages on request to its clients using the Hypertext Transfer Protocol (HTTP).
Web Server Attacks types:
>> DOS attack
>> Website Defacement
>> Directory Traversal
>> Misconfiguration attacks
>> Phishing Attack
>> Password Attacks
Why do people indulge in Hacking?
When someone hacks a computer or network system, it’s typically for one of three main reasons:
1) Hacking for fun:
Some hackers make attempts on computers, servers or network systems just for personal gratification. Others may feel that they need to prove something to their family and/or friends and hack a website or an account just to beat a challenge.

2) Hacking to steal:
Another reason to hack a system is to steal information or money. A large portion of hacking attempts falls into this category. Banks and large companies are common targets for hacking jobs but sometimes smaller companies or even an individual’s computer may be targeted.

3) Hacking to disrupt:
Some of the hackers or hacking groups target an organization just to mess up their business, create chaos and nuisance. These groups often try to make a statement with their hacking, demonstrate security inadequacies in systems or show general disapproval for the business itself.

Security tips to protect your website:-
1) Keep your software up to date
It may seem obvious, but keeping all software up to date is vital for keeping your site secure. The rule applies to both, server operating system and any software you that may be running on your websites like a CMS or some forum. Hackers attack a website as soon as they find any security loopholes in it.
In case you are using a managed hosting solution, you don’t need to be much concerned about applying security updates for the operating system as the hosting company takes care of it.
If at all you are using any third-party software on your websites such as a CMS or forum, you should immediately apply the relevant security patches. Most of the vendors have a mailing list or RSS feed detailing the website security issues. WordPress, Umbraco, and numerous other CMSs notify you about the available system updates as and when you log in.
2) SQL injection
SQL injection attack is a code injection technique wherein attacker uses a web form field or URL parameter to gain access to your database. When you use standard Transact SQL it is very easy to insert rogue code into your query, without your knowledge that could be used to change tables, steal information or destroy data. You can easily prevent this by using parameterized queries. Most of the web languages have this feature and it is easy to implement.
3) Error messages
Be careful with how much information you give away in your error messages. Provide bare minimum errors to your users, to ensure they don’t get enough information to leak secrets present on your server (e.g. API keys or database passwords). Don’t provide full exception details either, as these can facilitate making complex attacks like SQL injection lot easier. Keep detailed errors in your server logs and provide the users just as much information as they need.
4) Use HTTPS
HTTPS is a protocol used to provide security over the Internet. HTTPS ensures that users are talking only to the server they desire and that no one else can intercept or change the content they’re seeing in transit.
In case your users wish to keep any of their information private, HTTPS is highly recommended for the transaction/delivery of all such information. Of course, it implies to credit card and login pages (and the URLs they submit to) but it may be widely applicable to your entire website. For example, a login form often sets a cookie, which is sent with every other request to your site that a logged-in user makes and is used to authenticate all those requests. An attacker may steal this cookie to be able to perfectly replicate a user and hijack their login session. To defeat this kind of attack, you should always use HTTPS for your entire site.
5) Website scanning websites and plugins
You can use some plugins to scan your website for malware and you can also use some websites that can scan your website through Url.
>> Sucuri SiteCheck:
This is an online tool by Sucuri, one of the best WordPress firewall and security service. It thoroughly scans your website for any kind of spam injection, malicious code, website defacement, etc. Sucuri’s SiteCheck tool not only scans the URL you enter, but it also crawls other pages linked to it to for a thorough and fast scan.
>> Google Safe Browsing:
Google’s Safe Browsing tool enables you to see if a URL is marked unsafe to visit by Google. Google monitors billions of URLs and if at all they suspect any website spreading malware, they mark it as ‘unsafe’ to visit.
Getting an ‘unsafe’ tag by Google can ruin your website’s reputation completely as users coming from Google search or Google Chrome will be shown a warning page when they visit your website. If you are using Google Search Console, you will be warned whenever your website is marked as unsafe, along with instructions to get the warning removed.
>> Ninja Scanner:
Ninja Scanner is a fast, lightweight yet powerful antivirus scanner for WordPress and comes with a host of features to help you scan your blog for malware and viruses. You can use this plugin to scan your website and you can find it here.

6) File permission:
You should check your file permissions thoroughly to prevent hacking. WordPress-admin should be accessible only to you and your fellow bloggers (if any). You may use .htaccess in order to restrict access and allow only to select few IP addresses to access this directory. Wp-content contains everything and it is an extremely important folder. You must keep it as secure as possible. You shouldn’t let users access or browse any vital data. They should be only able to view and access certain file types like images (jpg, gif, png), Javascript, css, and XML.
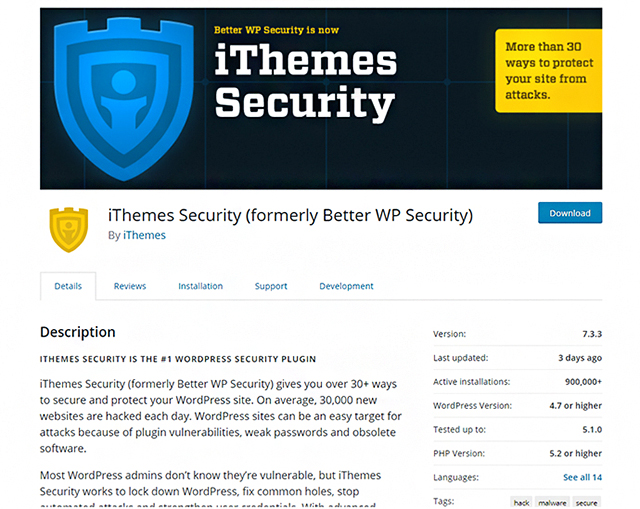
7) Security plugins:
iThemes Security (formerly known as Better WP Security) provides you more than 30 alternatives to secure and protect your WordPress site. On average, 30,000 new websites are hacked each day. WordPress sites can be a soft target for hacking attacks, thanks to plugin vulnerabilities, weak passwords, and obsolete software.
Most WordPress admins are not even aware that they are vulnerable. iThemes Security works to lock down WordPress, plug common holes, check automated attacks and strengthen the user credentials. This feature-rich WordPress security plugin can help strengthen WordPress. You can download this plugin from here
You may opt for free or pro version of this feature-rich WordPress security plugin.
Share your views/queries in comments and do share it with your friends if you find the article helpful!